Changing Landscape of IT Security in 2017
I have been in the IT business near its start. As a young kid I watched my father enthusiastically take on the transistor as the new disruptive technology at Fairchild (replacing valves). I watched him grow a large business in the IT space that in the end made him a lot of money. As a young teenager I watched engineers in my father’s firm create technology that made a large impact to the organisations that bought the products.
I was totally intrigued with the interface of computers and the real analog world.
There was a buzz. I was motivated at 15 to build my first computer from scratch using a Z80 processor, a rom, a clock source and a display. I wanted to scroll a message across the display. I used wire wrap to connect up the components, made my own power supply and whooshka. It didn’t work straight up but parts of it did. So with some help from my Dad’s engineers, I was guided me through the resolution of my mistakes. It did work but after programming several times (which took a “burn” of a ROM chip every time) I got distracted by something that had an operating system, which was much easier to reprogram and do lots of different things. It was called an Apple 11 (2).
The guys who started Fairchild, for whom my father worked, started Intel who made the Z80.
Working with Dad’s business I saw the impact and benefits of communication. If these computers could communicate, some awesome things could be achieved.
I was actively involved with modems while working with my Dad. Early modems in Telex machines, fax machines and computers used discrete tones to transmit data down phone lines. They were so slow compared with technology today and used discrete technology (lots of analog components) to create the modulation/demodulation (MODEM) processes.
I remember Dad introducing me to some guys he was in awe of at Codex (an American company from Boston). He was really excited about this. They had developed a technology that did the analog processing for modems in the form of digital processing rather than discrete components. That is, they could emulate complex analog circuitry with digital mathematics, called Digital Signal Processing (DSP). It wasn’t until I got to 3rd year university many years later that I understood how it all worked but I witnessed my first wave of virtualisation. Once the analog processes could be turned into a digital mathematical process the development of faster communications accelerated quickly with faster computer components.
Dad took on the Codex product from Boston and sold it throughout Asia making a fortune on the way.
The networks we created back then (1980’s) were application specific and typically contained to the bounds of that application or organisation. There were no links between organisations initially and if so it was head office to head office with batch communications of files etc. That is, it was contained and controlled.
Then there were some people in the US that thought it would be a good idea to interconnect several Unix mainframes so that they could swap ideas quickly around the various campuses they worked at. Now that was a winning idea!
Once computers connected together we had fun sending messages to other computers by taking control. We and wondered how the owner would feel if I did a Del*.* (delete everything on the computer). Early on it was not a big deal to reload the Disk Operating System (DOS) and start again. It was straightforward to transfer a program and start it on another computer also.
Today is another story.
We rely on computing resources to communicate, store all our information and control machines that can do magnificent things. They are incredibly small, have a lot of memory and use very little power. Like any human creation it can be used for good or evil.
We have amazing mobility with things like WIFI connecting at 3.8Gbps.
The challenge of protecting our information and control of significant assets has not really changed except its typically in the hands of computers and communications networks (instead of humans).
I have observed many make this transition to the digital age with little regard to security.That is, the security regimes they used to implement may not be implemented in the digital world. Decisions are primarily driven by the desire for increased speed, the need for a new technology or the chase for the new shiny object. All this is implemented with the focus on the reward without considering the protection that is necessary.
Today
We have a strong and growing security market within the IT industry. It changes quickly and is complex sometimes. It can be very rewarding for someone who is motivated as a simple string of commands can allow the user access to information or control of important infrastructure. Something very cheap can have a huge payout.
There are well established doctrines for implementing security within IT infrastructure. We do this every day in our business but as computer power, Artificial Intelligence (AI), and fast communications develop I see new risks.
I see risks evolving in two key areas. Broad propagation of cheap sensor type BOTS and big data analysis/influence. I work on the principle that if I am thinking of it as a possibility, it’s already a threat.
Sensor or Agent BOTs
BOTs, trojans and viruses are already out there so this is not new. What I see as a threat is the automated and intelligent placement of more capable BOTs (classed them all as one type of thing).
These newer BOTs gather or plant information, carry out functions via remote control, are good at self-destructing when detected and good at leaving no trails.
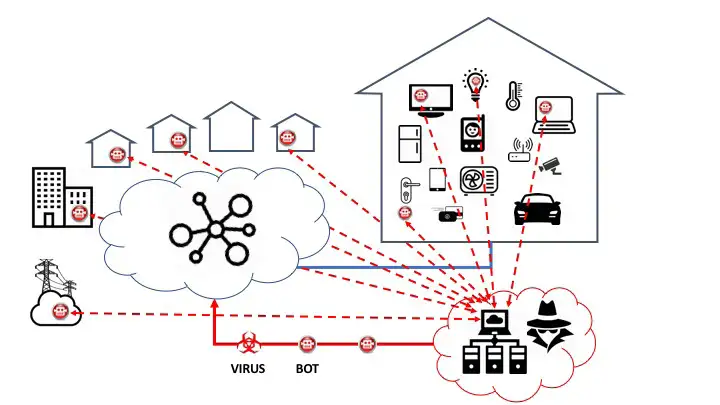
So this new threat is AI based systems constantly scouring for opportunities and leaving BOTs behind to collect data and then performs tasks when asked, maybe years after they have been implanted. These could be within your own personal equipment, the organisations equipment and in the physical environment.
In more recent times the security issues around Internet Of Things (IOT) has become an issue as these are being spread around the physical environment. These devices are light bulbs, security cameras, baby monitors, door locks, computer monitors, computer mouse, card swipe readers, thermometers, WiFi access points, printers, coffee machines, fridges, TV game consoles, fire detectors, transducers, USB drives, movement detectors, power outlets and so on.
I have heard stories about senior politicians and executives being issued a laptop, tablet or phone for company use while overseas. These laptops are promptly shredded upon return. Yes, shredded! Why? There are stories of the microcode of these devices being compromised. The microcode is the basic software you don’t see that tells a compute platform (phone, tablet, computer etc) or components how to set itself up before the operating system loads (IOS, Android, Windows etc). The microcode compromise can be buried in sub components of a computer so the BIOS or security software does not even detect it.
In recent times this sort of activity would be from a focused, motivated and resourced effort. However, I see the threat coming from the automation of this and it being more widely available.
Data Mining
It’s one thing to have a specific piece of info. Another story can be seen with a long term look at data or even a glance back at old data. This is what I call the differential and integration affect, like the mathematical differential/integration where analysis is made of a dynamic situation.
I will give you a real-world situation for example. We implement technology today for the likes of shopping centres that want to implement WiFi for marketing purposes and provide their customers with access to the internet for free. The client loads an “App” onto the phone and gets free internet while in the bounds of the shopping centre.
With this App running we can track the shopper, Mrs X for example, around the property. We can tell where she parked, which entrance she came in, where she stopped, where she walked and from the App what she might be interested in buying. The APP may suggest bargains on the property at shops she is close to or direct her to the shop she seeks.
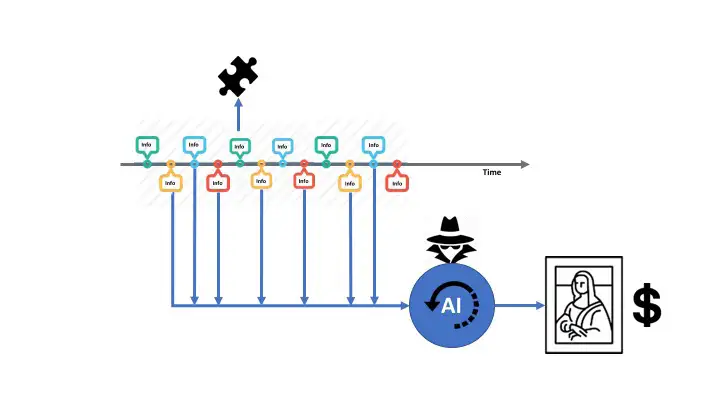 But take a big data look at this. If we look at all the data that is collected for Mrs X over a long period we can see some interesting behaviour. We can ascertain the following as an example:
But take a big data look at this. If we look at all the data that is collected for Mrs X over a long period we can see some interesting behaviour. We can ascertain the following as an example:
- If she is having trouble with her hair dresser by noticing what she does after visiting one. Does she visit another straight after?
- What are her shopping days, what days does she do the food shopping for example.
- Who is with her on specific shopping days. We can ascertain a common set of MAC addresses that are nearby her when she shops and then track where they went. It’s easier if the people close to her are on the wireless network also.
The data that is left behind from an individual can be useful information. If you are a CEO of company negotiating a big contract, how you behave and where you have been when cross correlated with other targets could be crucial information to a competitor. In the past this would require a lot of resources. In the digital world, this can be achieved far more easily and while today it would take some resourcefulness its getting easier very quickly. The tools are building tools!
The challenge with this threat is that the analysis is done somewhere else but it’s now more a threat due to proliferation of information picked up potentially by plethora of BOTs, small active devices, drones and powerful big data computing. The key assets here are the data mining algorithms!
For example, with our WiFi analysers I can tell which AP’s your phone has connected to in recent times. So, I can tell which hotel you stayed at without you seeing me! Big deal, you say, but that information in concert with many other snippets may tell a considerable story.
Early November 2016 news hit that the Red Cross had exposed all its patient records for the last 10 to the internet. I am sure this information would have been taken because of the automation. When you give blood, you have to provide some very sensitive information like sexual preferences, other partners, medical details and history of diseases. So, could this information be used in the future? If a politician or a CEO was a blood donor and has something to hide, then they could be compromised. The problem is you may never find out what leak caused what damage (if the leak was detected).
A month earlier, Medibank details with patients’ records and doctors’ notes were found exposed on the internet. They claim the breach was noticed early and fixed but I would expect the information is elsewhere.
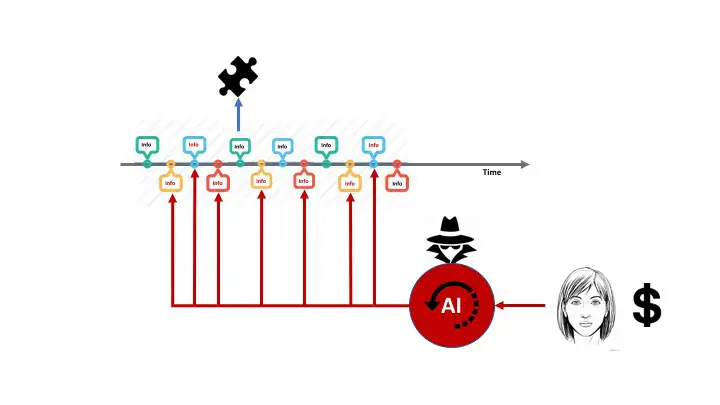
Information Integrity
In the above examples the information flow is primarily one way, into the wrong hands. I have recently started wondering if these BOTS could also implant incorrect information. I have heard uncorroborated “industry speak” in the last 6 months where researchers felt that their work had been copied but also that the research data had been tampered. Some of these research projects take 5 or more years and if there is no confidence in the data integrity the entire project may need to be scrapped.
 There was another recent example (and documented one) where a private organisation was about to undertake a significant project for the Federal Government. Things were going well until a couple of people from Australian Signals Directorate (ASD) turned up on their door. The CIO and the management team were told that most of their IT&C infrastructure was infiltrated and they could not proceed with the government work unless things were cleaned up. The CIO and his team had thought they had followed best practice.
There was another recent example (and documented one) where a private organisation was about to undertake a significant project for the Federal Government. Things were going well until a couple of people from Australian Signals Directorate (ASD) turned up on their door. The CIO and the management team were told that most of their IT&C infrastructure was infiltrated and they could not proceed with the government work unless things were cleaned up. The CIO and his team had thought they had followed best practice.
The company was so infiltrated, they had to throw everything out. They had to build a new IT&C infrastructure from scratch and could not even copy data or documents! This put them back 18 months!
Government
The Federal Government has some strong doctrines for managing secure documents and information. They have regimes for classifying information (“Top Secret” for example). They also have a regime for classifying the people who can have access to the various levels of information. This one doctrine operates over all Federal Government agencies and the laws that govern this have serious consequences for those involved in a breach.
There is a lot at stake of course, maybe people’s lives. These processes are sometimes inconvenient, slow things down and can be difficult to work with. It is not a perfect system either as information leaks but it gives organisations the disciplines to manage themselves and work with other departments.
During the US election campaign the email issue with the Clinton Democratic campaign was probably compromised. The Clintons built an email server directly exposed to the internet (no proper security to screen it) and it’s no surprise that the emails (or the ones someone wanted to expose) ended up on Wikileaks. We sat around the office one day and researched how that email server was set up and all shook our heads in disbelief of the level of stupidity. I started to think it was so stupid it was deliberate. If we did that for a client I suspect we would be laughed out of the industry. Some of those emails were damning and I am sure most people giving opinions had not even read them. Then again the Clinton camp cannot refute the details of the emails, can they?
All State Governments in Australia don’t have a regime (laws and process) like the Federal Government. They might have some laws and standards but not at the same level. It means that individual departments implement their own systems and they are generally overridden when it slows things down. I have seen doctors and other senior people email confidential details like patient records or cabinet documents via private email to speed things up. They do it because they have to get something done and they may be arrogant.
What they don’t realise is that the document is on their laptop, the email went via China or other overseas email exchange servers and is on the recipient’s laptop. So many opportunities for security breach! Therefore, Police won’t trust Human Services or the Department of Health etc. The other problem is that the piecemeal systems that are set up may not be exposed to FOI or discovery from an Ombudsman or similar.
The Federal Government is in the process of updating the privacy laws in Australia at the time of writing this article. At this point it won’t apply to state governments and firms with a turn over of less than 3 million.
Non-Government
Many non-government organisations are in a similar situation as state governments. Many of the ASX top 500 companies don’t have an IT security team and for those that do I have heard only ten or twenty of them have a competent team. I have met many IT security people in large companies and I would not have much confidence.
The ones that are competent usually shake their heads in frustration at the lip service that the “C” level people pay to IT&C security and who typically undo all the good work of security teams! One of the biggest issues for them is that senior management often think their rules don’t apply to them which sets up a bad culture.
The problem for non-government organisations is that if a client is badly or adversely affected then the Directors will be ultimately liable! Now if I was a clever nasty person I could find some info, inflict damage to a client (black mail etc) then inform the client for a fee how we got the info so he could litigate. If I thought of it then??
What Can You Do?
I have provided some steps or ideas to provide protection for you and your organisation.
Protection
- Create some misinformation. So, when it turns up you know where it came from.
- Be aware of where your critical information is, who has access to it and where it is backed up.
- Constantly keep your security systems up to date. If you skimp it will leave a hole. If you can’t afford it store information close to you.
- Split up the information and all the associated password and account linkages. You might need several email accounts. I.e. If one is breached, then the loss is contained.
- Federal agencies have some good disciplines. They place people into classification groups and then manage information differently within the classification groups.
- Read the ASIO/ASD ISM document set, especially the executive guide. It’s constantly updated, it’s free and it’s written by some real experts.
- Use sandboxed applications-based operating systems for sensitive activity. For example, IOS where apps are downloaded from the iStore.
- Assume all information given to state governments is public information (until they change their ways).
- Other than major Federal Government agencies, assume all the super confidential information you have given to an organisation you might trust, is in the public domain.
A cool thing about our digital revolutions is that things advance quickly and there is a lot of rejuvenation. For example, a new phone every year for some people. This refresh can have the effect of washing away any infiltrations. The trick is not to take the nasties with you when migrating.
