NDBS and What It Means For Your Organisations IT
I am frequently getting asked by our clients what needs to be done for the new privacy laws that came into play this year. These questions are typically coming from CIO’s, senior IT professionals, company directors and business owners. Many of these people report to, or work with a board, who are becoming increasingly concerned about the organisations behavior around collection and storage of private information.
The new privacy laws that began on the 22nd February are known as the Notifiable Data Breaches Scheme (NDBS). This comes under Part IIIC of the Privacy Act 1988 (Privacy Act). It essentially deals with data breaches surrounding loss or unauthorised disclosure of personal information. I am not going to dispense legal advice but can share a little of what I have learnt because I am a Fellow of the Australian Institute of Company Directors, I run a company and I also work in the ICT space.
What I am noticing is that the NDBS is bringing attention to the whole privacy act and therefore to the state of an organisations information technology system. The privacy act and the NDBS are law and to determine how this relates to your organisation I would advise seeking some legal advice. I can refer readers to several firms that I have worked with that are very knowledgeable about this space.
But what about how this relates to IT systems? We can help out here. What I’d like to focus on discussing here is how an organisation stores and transfers its information.
A recent international report cited that 68% of organisations operating applications in the cloud are bringing them back to their own infrastructure (private cloud or infrastructure as a service). One of the main reasons is to allow them to directly manage or secure their critical information, as sometimes with cloud storage there is no absolute certainty on where it is located or who can look at it. This is what Laminar does as well. The trend is to use the cloud to create the elastic infrastructure to deal with peak loads or store/manage less sensitive information (such as email).
In modern IT systems there are a mix of solutions in use typically, “cloud” in its many forms, on premise IT and mobile IT. That means data is spread around on site, off site (virtual or physical infrastructure) and with service providers. This could also encompass something that is written down and then photographed on a corporate device. The information security situation will vary for each organisation so there is no “one size fits all” solution. It’s important for you to be aware where your data is stored, where the most confidential data is located and how it is accessed.
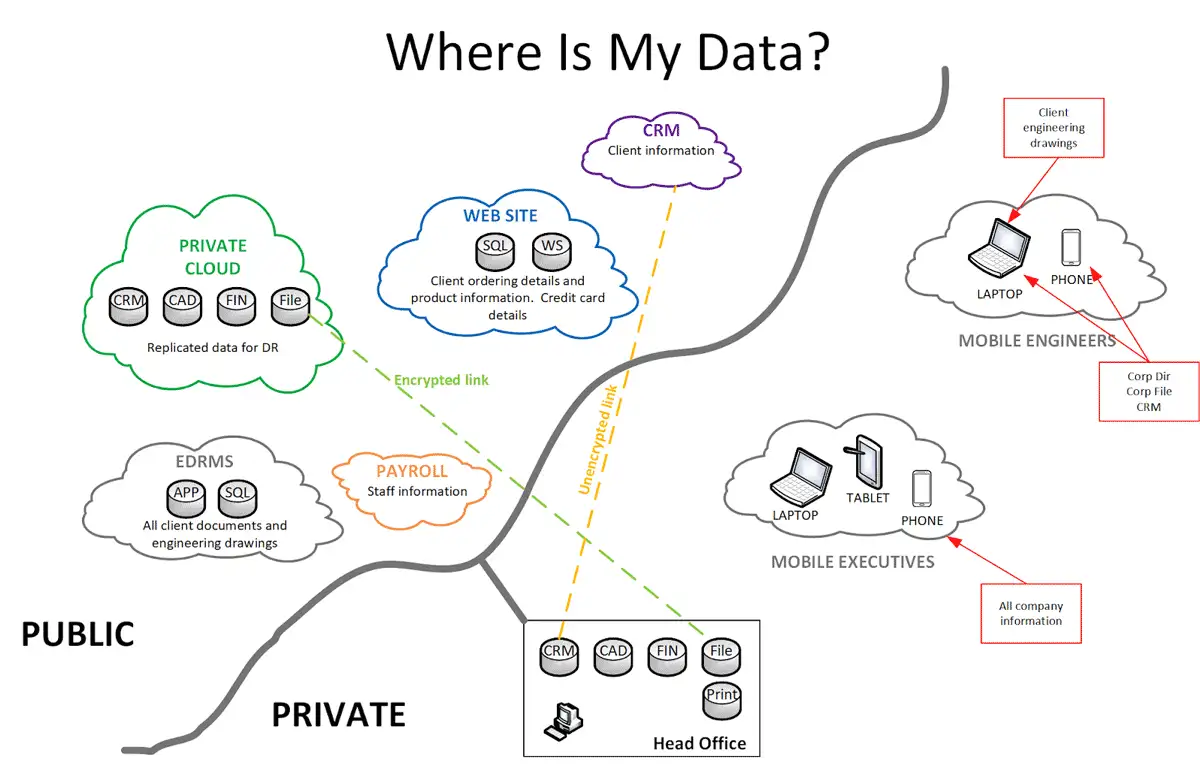 Image: Example of how your information may be stored, do you know where your data is?
Image: Example of how your information may be stored, do you know where your data is?
The latest Spectre and Meltdown cyber threats would worry any cloud service user! That is, there is a threat that one virtual machine from one company, could access private information of another company running totally separate virtual infrastructure. Have you formally asked your cloud providers what they are doing about this threat, and then formulated your plan? Many cloud operators have started using the hardware in a way to limit risks with Meltdown and Spectre but this has come at a performance cost. I’d suggest you discuss with your IT professional or feel free to call us to discuss.
In my experience even with adequate IT systems, I also see many cyber threats arise due to human behaviour. Sometimes its due to peoples blind trust in technology, speed (growth or change in an organisation), sloppy practices around data safety, passwords and security, and management’s view that they are not the problem. I have frequently seen passwords written, unsecured devices, or USB’s holding important data just lying around. Would you as an individual or company just leave cash lying around? And expect that it is safe and still be there when you come back? Then why do you leave critical data lying around? What disciplines do you implement to ensure your data is safe and that the “human” element of your organisation are aware of these risks and disciplines?
Cyber threats are now a part of the challenge of running a business but simple data loss due to technical issues or human behavior are the other. An employee leaving a laptop in the cab or Uber, losing a USB stick that had client information on it, letting children play with work phones and lax password disciplines are other things that may create opportunities for cyber attacks or loss of information triggering a NDBS event.
We recently helped a client move offices (an accounting firm and therefore large amounts of personal data stored) and we were responsible for the move. We accounted for every computer, hard disk, USB Drive, server and storage system. Laminar then moved them using our resources, and thoroughly checked them once at the new offices. We managed this carefully due to concerns that any lost equipment would trigger a NDBS event and an embarrassment for our client.
Questions to Ask
Every enterprise is different but to help I have outlined below some basic questions to ask yourself or within an organisation. This is relevant to both the securing personal information for the NDB Scheme and also for best practice storage and securing of data for your organisation:
The 4 W’s
Who and what has access and control of it (staff/contractors/clients/vendors SAAS platforms etc) password. For example we (Laminar) and some of our clients only allow access to information on controlled devices. They may engage MDM platforms or restrict access to some information to certain types of authenticated devices. Make sure that there are no shared accounts and that the access rights are as required.
What info do you store and keep (it can be electronic or paper pics etc)
When? Are you backing up enough and at the right times?
Where is it stored at all times, main data set, back up, recovery etc.
How is your security?
Just do the basics right. There is a lot in this and this is where you need to give us a call on (07) 3177 0899.
- Set up a syslog server to record events from networking and security system (helps diagnose and helps with audit trail during investigation
- Review the business continuity plans, disaster recovery strategies and check they are still suitable. Remember “Lost” personal information may trigger a NDBS need to notify clients and the commissioner
- All contractors and subcontractors to sign Non-disclosure agreements. Review the information privacy provisions of the cloud service providers you use (SAAS, IAAS, PAAS etc)
- Create a plan! It’s not a matter of if, but when! If you create a plan now, when the organization is in duress, well documented processes can take the thinking out of it and help reduce the risk
- Credit card payment systems need attention and PCI compliance may be an issue. Maybe just use the banks machine
- Keep everything patched. Whenever a vulnerability is found everyone then knows how to make use of the vulnerability. So if you avoid patching remember the rest of the world has told the hackers how to get in!
- Director audits from time to time – Check-ins
- Update staff IT policy manuals or documents
- Conduct basic staff cyber security training. There are online courses and also more elaborate on site training which may be useful for senior staff
- Consider what you are taking with you when you travel overseas. Do you really need the laptop with all those client records or sensitive engineering drawings on it? Would a simple IPAD be sufficient for emails?
What could represent a possible security breach?
Here is a quick sample list:
- USB device lost
- Laptop left in a cab (strong hard disk encryption would get around this problem but who does that?)
- Server stolen from the office
- Backup tapes not accounted for
- Trusted 3rd party fails in some way (OS supplier has a breach)
- Shadow IT operations use a service that is dubious
- Accidental email of a data file by an employee.
Commonly Sensitive Data Sets
Some data sets that are especially sensitive that if released for general consumption could cause harm. Here are some common ones.
- Medical records
- Staff records
- Tax file numbers
- Credit card details
- Passport details
- Photos of clients or staff
Some food for thought to assist you in managing your organisation through this technical and constantly evolving era. If you are interested in further information, here is a great reference: Office of the Australian Information Commissioner and for any technical queries on what you and your organisation can do to better secure your data please don’t hesitate to give us a call on (07) 3177 0899.
