Laminar’s SIEM Service
Laminar has released a new Security Information and Event Management (SIEM) service. This technology is used to help manage cyber security. This technology traditionally has been used within very large IT&C infrastructure systems, such as that used in banks and large government departments. It has been very expensive to implement and requires a great deal of skill to operate and maintain. Thus making it difficult for most organisations to acquire. It is however becoming a critical resource in protecting an organisation from cyber threats.
A SIEM system is one that aggregates data produced by security devices (eg: firewalls), network infrastructure (eg: switches), systems (eg: Domain Controllers) and applications. This data is typically log data, but can also be other forms such as telemetry and contextual data about users, threats, vulnerabilities and assets. The data is stored and analyzed using heuristic and AI tools to keep an eye out for unusual activity. The system is looking for traditional cyber security mischievous activity from specific sources (such as a firewall) but also more sophisticated attacks by correlating information across many client platforms or data feeds.
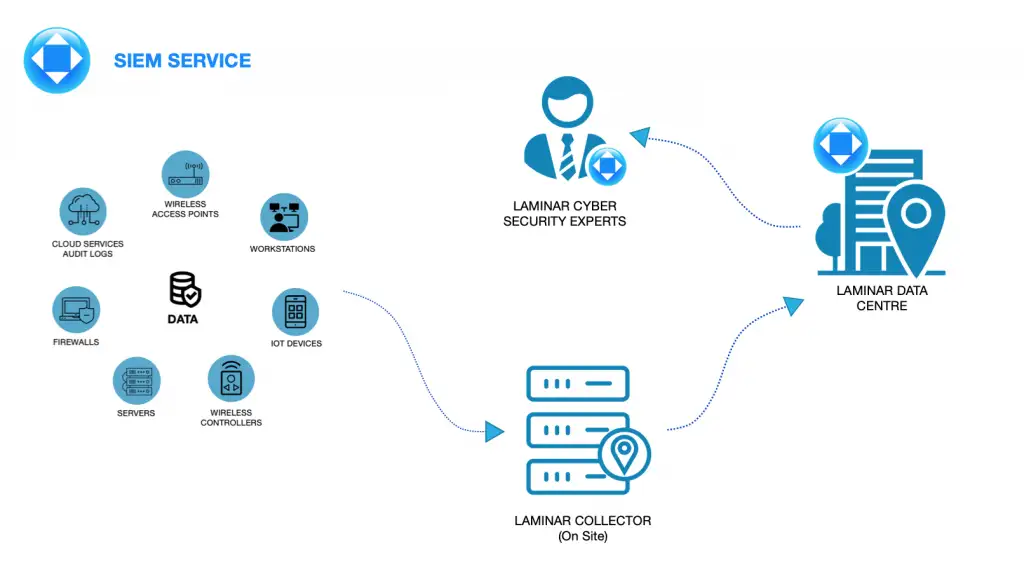
Laminar is now offering the same service in a more affordable manner, hosted within our data centre and managed by our cyber security experts. Key infrastructure assets send information to a Laminar collector, located on the client’s site(s). The collector aggregates the information and sends it securely to our data centre.
The key attribute of the SIEM is its ability to correlate and analyze data from many streams. For example, a switch may record a port “flapping” which in itself is not a major concern in many cases. However a port “flapping” correlated with many failed attempts to connect to a PC and a server, with a user connecting to a suspicious unsecured web site would be a major concern.
The data is stored for an agreed period in Laminar’s Brisbane data centre facility and is retained in case there is an incident and subsequent investigation. All data, analysis and reporting is retained within that data centre. Some clients will find the service useful even if they already store logs, as it provides some governance around incident reporting. That is, if internal logs of data are tampered with, there is a second source of the “truth” located off site.
We have just finished trials with many clients including large private schools, a federal government organisation and a large accounting firm. One of our trial clients found an issue within two hours of connecting to the Laminar SIEM even after recent PEN Testing.
The Laminar SIEM service is being offered in three tiers, that build upon one another:
SIEM Level 1 – Base level: This service is the entry level offering whereby Laminar simply records data within the SIEM framework. Clients can connect and read or review the data and do some basic analysis themselves. In the case of an incident, the system will be made available to investigators who can use the extensive tools we have or use their own. Pricing for this service level is based upon the size of the customers infrastructure, the level of detail needed to gather (based on risk profile) and how long data needs to be retained.
SIEM Level 2 – Analysis and Alert: Building on the Base service, the SIEM system will actively monitor and analyze the data streams using the heuristic and AI tools.
These tools improve and adapt in time. The client can elect to receive alerts directly and then use their login Laminar will provide so they can review the situation. The system offers the ability to create the following reports:
a) Out-of-the-box pre-defined reports supporting a wide range of compliance auditing and management needs including – PCI-DSS, HIPAA, SOX, NERC, FISMA, ISO, GLBA, GPG13, SANS Critical Controls
b) To meet GDPR requirements: Personally Identifiable Information (PII) can be obscured based on an administrator’s role.
SIEM Level 3 – Reaction: Building on the previous two levels, the Laminar help desk and engineers will respond directly to alerts from the SIEM or problems that are raised with us. In this case the Laminar Help Desk or Network Operations Centre will be monitoring client systems and will react in accordance to client needs.
Our tools enable unified data collection and analytics from diverse information sources including logs, performance metrics, SNMP Traps, security alerts and configuration changes. The Laminar SIEM essentially takes the analytics traditionally monitored in separate silos from Security Operations Centre (SOC) and Network Operations Centre (NOC), and brings that data together for a more holistic view of the security and availability of the business. Every piece of information is converted into an event, which is first parsed and then fed into an event-based analytics engine for monitoring real-time searches, rules, dashboards and ad-hoc queries.
The Laminar SIEM uses Machine Learning to detect unusual user and entity behavior (UEBA) without requiring the Administrator to write complex rules. Our SIEM tools help identify insider and incoming threats that would pass traditional defenses. High fidelity alerts also help prioritize which threats need immediate attention.
Each client has their own partitioned SIEM system (multi-tenant architecture) and isolated from others.
Should this SIEM service sound like something you would like to trial or implement, please give us a call to discuss on (07) 3177 0899.
