Working Remotely and Working Safely
Enough has been said about COVID and what that means to businesses. We have rapidly moved to a mobile workforce that can work from anywhere. What we need to think about now though is the potential increase of data breach points for company data. We frequently talk about data breaches as a hacker compromising the corporate network, but what about all the personal devices that now have company applications installed on them or users who are now using SaaS applications (Xero, MYOB, Slack, Zoom, WebEx or Box etc). The attack surface has dramatically expanded. Think about how many files have been shared or downloaded from these platforms onto untrusted devices. Suddenly, we have a data breach that we are not aware of.
Very few companies are fortunate enough to be fully cloud deployed and most on-premise companies have at least some cloud usage by now. The struggle is about how to control all of this while allowing flexibility for users to get work done. If you make it too hard they will just go around your security and create their own solutions. Remember that this is not just a technology problem you also need to ensure your users are involved. Ensuring users understand the need to comply with these restrictions, following company security policies and following good security practices such as secure storing of passwords.
So can we meet our security requirements and keep our users happy? The answer is simple; conditional access, but what does this mean to different people…
For Security Teams – Depending on the end users device and how compliant it is to the organisation’s security requirements dynamically defines what users can access.
For End Users – Users are able easily access organisations resources without compromising security.
Scenario: The national sales manager is travelling for a very important meeting with your organisation’s biggest client the next morning at 8am. That night the corporate provided machine dies and no longer turns on. With this information you receive a very disgruntled phone call saying that you are responsible and you need to provide a solution.
Normally this would be a disaster, but what if all they required is an internet connected device to get them going. We could beg, borrow or buy a cheap computer and treat it as another BYOD device.
So what does this design look like?
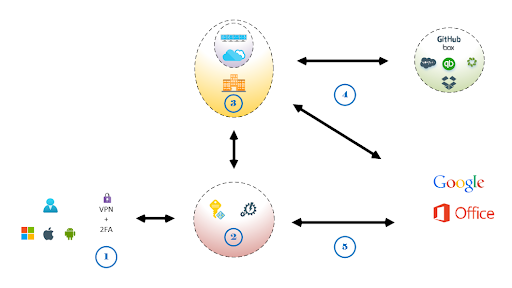
Step 1 – The user connects using either; Corporate managed device, Enrolled device or untrusted device
Step 2 – Security evaluation is undertaken of; user credentials, device type and user location
Step 3 – If the user, device and location meet the conditions users are allowed to access organisations internal resources. This could be Remote Desktop Services(RDS), Citrix, Virtual Desktop Environment(VDI) or newer cloud hosted desktop environments.
Step 4 – Conditions in Step 2 restricts login to external 3rd party services to authorised resources in Step 3. Users never see credentials and they are unable to recover the passwords. Any downloads and information is then stored on Step 3 controlled services.
Step 5 – If users are using untrusted devices users are still able to access productivity services without the ability to download information allowing for mobile device usage.
With this scenario our Sales Manager is able to login and access their work from any internet connected PC, MAC or tablet. We have maintained the users functionality and most importantly we achieved this while maintaining security. We have now implemented a Zero Trust (1) security philosophy where we always control the outcomes.
The key piece here is Step 2 where the decision conditions are made using a decision engine. At any time we can tighten or relax restrictions to suit an organisation’s requirements and this controls access to external websites. In Step 3 we are able to deploy resources either onsite or in the cloud to scale to meet requirements. This provides a read-only interface where users are provided with a screen and ensures no data leaves our control.
This scenario shows that whilst working from home brings a variety of challenges, it is possible to find a solution that balances security concerns with the needs of the user. Through the above and good security practises we are able to maintain safe and secure access for users.
